This article only applies if you don't have an IdP set up. If so, managing password policies should be done in the same place as the other identity related business rules.
Prerequisite : Having an LDAP server running and integrated with Keycloak, for example as described in this great article from Gravitonian or this documentation from Kristijan Conkas.
Configuration :
Go to
http://<host:port>/auth/admin/alfresco/console/#/realms/alfresco/user-federation
NB : for this article I'll be using the default realm "Alfresco" you may want to modify the url to work with your realm.
For example: if you followed Gravitonian's article mentioned earlier, the url will be
http://localhost:8080/auth/admin/alfresco-dbp/console/#/realms/alfresco-dbp/user-federation
Click on your LDAP user storage provider (in my case asapids) :
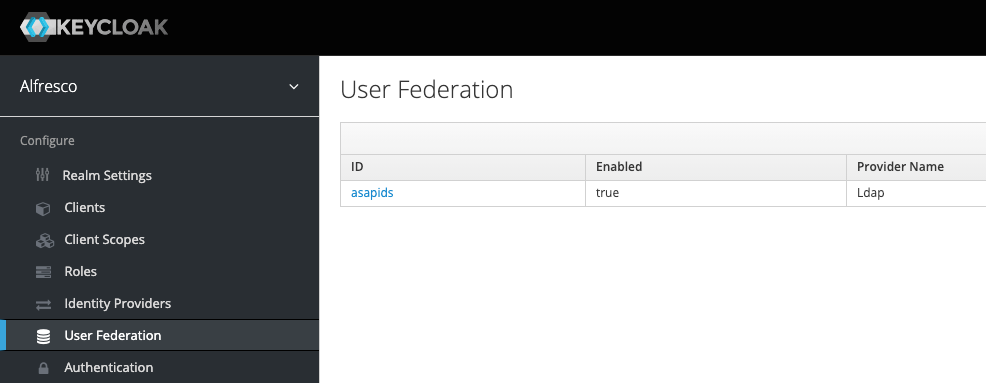
On your LDAP user storage provider configuration page, make the following configuration changes :
- Edit Mode : WRITABLE
- Bind Type (or Authentication Type depending on the version installed) : simple
This shows the Bind DN and Bind Credential fields, that you want to fill with the credentials of a DN having the rights to modify the user/pass attributes of the related LDAP directory (the admin for example).
Finally enable Validate Password Policy in the Advanced Settings and click Save.

Now you can go to the Authentication menu and click on the Password Policy tab.
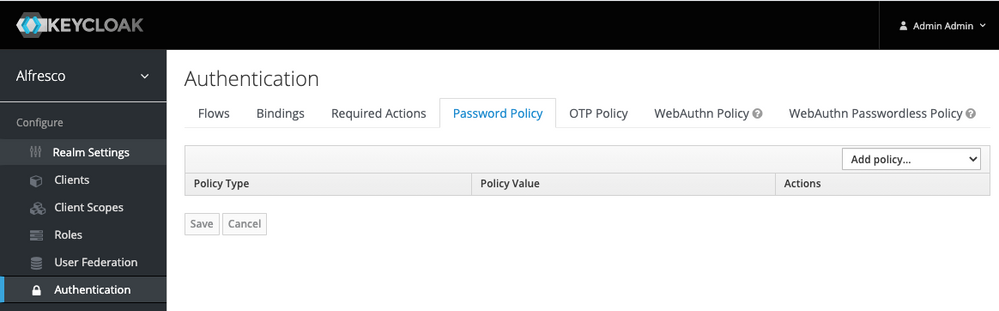
You can then add multiple Password policies (only the Regular Expression can be used multiple times).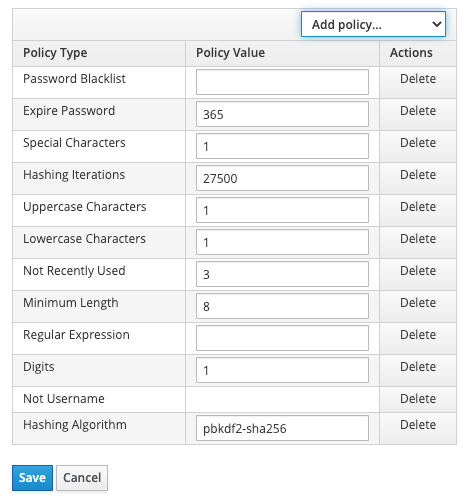
For more information, please visit Keycloak's related documentation.
NB : The Not Recently Used and Expire Password policies don't work with LDAP. Keycloak, can't retrieve the server information as of today. Indeed, it would be too heavy to maintain the code for every possible LDAP implementation. And also because the policies are applied at password renewal, not at login.
In order for a user to modify it's password OOTB, he has to visit
http://<host:port>/auth/realms/alfresco/account/password




