Alfresco MTLS Configuration Deep Dive
- Alfresco Hub
- :
- ACS - Blog
- :
- Alfresco MTLS Configuration Deep Dive
Alfresco MTLS Configuration Deep Dive
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
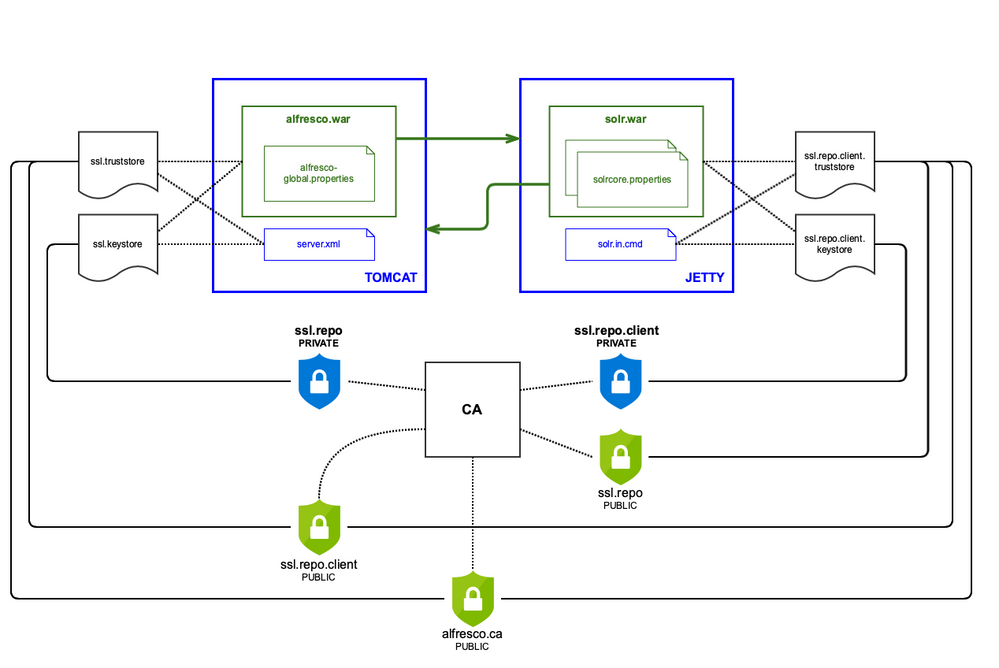
When setting MTLS configuration between SOLR and Repository, some steps need to be done:
- Generate certificates for Repository (ssl.repo) and SOLR (ssl.repo.client) using a CA (alfresco.ca)
- Configure Tomcat Repository in order to manage incoming HTTPs requests from SOLR
- Configure Alfresco Repository WAR in order to build request to Jetty SOLR
- Configure Jetty SOLR in order to manage incoming HTTPs requests from Repository
- Configure SOLR WAR in order to build requests to Tomcat Repository
1. Generating certificates
Several certificates are required:
- alfresco.ca is the public certificate of the CA used to generate ssl.repo and ssl.repo.client certificates
- ssl.repo is the certificate (private and public) to be used for the Repository
- ssl.repo.client is the certificate (private and public) to be used for SOLR
Keystore (private keys) and Truststore (public keys) files are required for the Repository and SOLR. Supported formats for these stores are JKS, JCEKS and PKCS12. The contents for every store are described below:
- Repository Keystore (ssl.keystore) contains ssl.repo private key.
- Repository Truststore (ssl.truststore) contains alfresco.ca and ssl.repo.client public keys.
- SOLR Keystore (ssl.repo.client.keystore) contains ssl.repo.client private key.
- SOLR Truststore (ssl.repo.client.truststore) contains alfresco.ca, ssl.repo and ssl.repo.client public keys.
These files can be generated manually but it's easier to use the Alfresco SSL Generator Tool.
2. Configuring Tomcat Repository
Tomcat Repository is handling secure tracking requests from SOLR WAR, so a new Tomcat Connector must be added to /usr/local/tomcat/conf/server.xml file.
<Connector port="8443" protocol="org.apache.coyote.http11.Http11Protocol"
connectionTimeout="20000"
SSLEnabled="true" maxThreads="150" scheme="https"
keystoreFile="/usr/local/tomcat/alf_data/keystore/ssl.keystore"
keystorePass="kT9X6oe68t" keystoreType="JCEKS" secure="true"
truststoreFile="/usr/local/tomcat/alf_data/keystore/ssl.truststore"
truststorePass="kT9X6oe68t" truststoreType="JCEKS" clientAuth="want" sslProtocol="TLS">
</Connector>
3. Configuring Alfresco Repository WAR
Alfresco Repository WAR requires to be configured in order to build secure requests to Jetty SOLR when performing searching operations. Add following settings to /usr/local/tomcat/shared/classes/alfresco-global.properties file.
solr.port.ssl=8983 solr.secureComms=https dir.keystore=/usr/local/tomcat/alf_data/keystore encryption.ssl.keystore.type=JCEKS encryption.ssl.truststore.type=JCEKS
Inside dir.keystore folder following files are required: ssl.keystore, ssl.truststore, ssl-keystore-password.properties, ssl-truststore-password.properties.
4. Configuring Jetty SOLR
Jetty SOLR is handling secure searching operations from the Repository. Following configuration is required to be added to SOLR starting script solr.in.sh (Linux) or solr.in.cmd (Windows) under folder /opt/alfresco-search-services/
SOLR_SSL_TRUST_STORE=/opt/alfresco-search-services/keystore/ssl.repo.client.truststore SOLR_SSL_TRUST_STORE_PASSWORD=kT9X6oe68t SOLR_SSL_TRUST_STORE_TYPE=JCEKS SOLR_SSL_KEY_STORE=/opt/alfresco-search-services/keystore/ssl.repo.client.keystore SOLR_SSL_KEY_STORE_PASSWORD=kT9X6oe68t SOLR_SSL_KEY_STORE_TYPE=JCEKS SOLR_SSL_NEED_CLIENT_AUTH=true SOLR_OPTS="$SOLR_OPTS -Dsolr.allow.unsafe.resourceloading=true -Dsolr.ssl.checkPeerName=false -Dsolr.data.dir.root=$DIST_DIR/data -Dsolr.solr.model.dir=$DIST_DIR/data/alfrescoModels"
5. Configuring SOLR WAR
SOLR WAR requires to be configured in order to build secure requests to Tomcat Repository when performing tracking operations. Following lines must be added to both SOLR cores (alfresco and archive) in the following locations:
- /opt/alfresco-search-services/solrhome/alfresco/conf/solrcore.properties
- /opt/alfresco-search-services/solrhome/archive/conf/solrcore.properties
alfresco.secureComms=https alfresco.port.ssl=8443 alfresco.encryption.ssl.truststore.location=/opt/alfresco-search-services/keystore/ssl.repo.client.truststore alfresco.encryption.ssl.keystore.provider=JCEKS alfresco.encryption.ssl.truststore.type= alfresco.encryption.ssl.keystore.location=/opt/alfresco-search-services/keystore/ssl.repo.client.keystore alfresco.encryption.ssl.truststore.provider=JCEKS alfresco.encryption.ssl.truststore.passwordFileLocation=/opt/alfresco-search-services/keystore/ssl-truststore-passwords.properties alfresco.encryption.ssl.keystore.type= alfresco.encryption.ssl.keystore.passwordFileLocation=/opt/alfresco-search-services/keystore/ssl-keystore-passwords.properties
Troubleshooting
If you are experimenting problems when searching from Alfresco or Share web applications, check steps 3 and 4.
If you are experimenting problems when indexing / tracking from SOLR web applications, check steps 2 and 5.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Ask for and offer help to other Alfresco Content Services Users and members of the Alfresco team.
Related links:
- Alfresco Community Edition 23.2 Release Notes
- Decommissioning of Alfresco SVN Instances
- Summarization of textual content in Alfresco repos...
- ACS containers and cgroup v2 in ACS up to 7.2
- Migrating from Search Services to Search Enterpris...
- Alfresco Community Edition 23.1 Release Notes
- Integrating Alfresco with GenAI Stack
- Achieving Higher Metadata Indexing Speed with Elas...
- ACA Extension Development Javascript-Console & Nod...
- Hyland participation in DockerCon 2023
- Alfresco repository performance tuning checklist
- The Architecture of Search Enterprise 3
- Alfresco Identity Service End of Life
- Using ActiveMQ with Alfresco 7.4
- Offline/parallel re-indexing with ElasticSearch
We use cookies on this site to enhance your user experience
By using this site, you are agreeing to allow us to collect and use cookies as outlined in Alfresco’s Cookie Statement and Terms of Use (and you have a legitimate interest in Alfresco and our products, authorizing us to contact you in such methods). If you are not ok with these terms, please do not use this website.