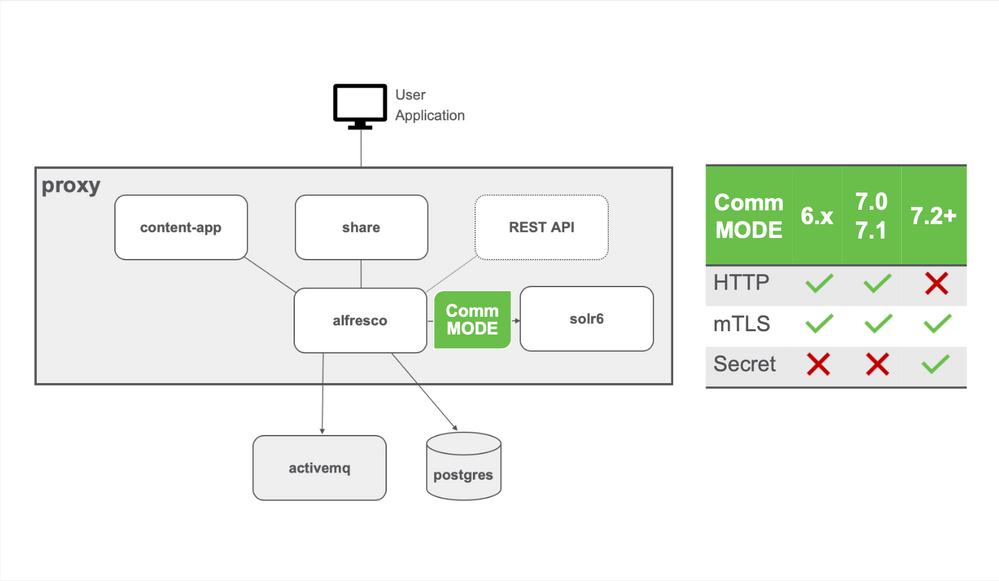
In this blog post we deal with the most important configuration change introduced with the release of ACS 7.2. Since the plain HTTP communication mode between Alfresco Repository and Search Services is deprecated, you may need to adjust your configuration to use one of the supported communication modes: Mutual TLS or Secret Header.
A regular Alfresco deployment includes a set of services that provide all the required functionality for the ACS stack. This blog post focus on the communication mode between the Alfresco Repository and the Search Services, which is based on Solr 6.
There are three different communication modes available:
- 'none' uses the plain HTTP protocol without authentication, so you need to protect this communication with an external configuration, such as NGINX Web Proxy configuration, to prevent external access to Repository and Solr 6 endpoints.
- 'https' uses the Mutual TLS protocol, where you need to create a set of keystore and truststore files, including digital certificates, that ensure authentication between the two services
- 'secret' uses a common secret word in a special HTTP header, so that communication is not using authentication but is protected by the configuration of this secret word in Alfresco and Search Services
The modes "none" and "https" are available for ACS 6.x as well as for ACS 7.0 and 7.1. As of ACS 7.2, only the modes "secret" and "https" are available.
Call to Action
Notes on Secret mode configuration
When applying configuration to Search Services, using environment variables (for ZIP Distribution deployment and also for Docker / Helm deployment) is required.
-Dalfresco.secureComms=secret
-Dalfresco.secureComms.secret=password
When using SOLR command line tools, it's required to use alternatively HTTP REST API invocations. For instance, the replacement for bin/solr status is:
$ curl --location --request POST 'http://localhost:8983/solr/admin/cores?action=STATUS&wt=json' \
--header 'X-Alfresco-Search-Secret: secret'
Additional details
Additional details on the configuration and a sample upgrading process is described in the following video recording.

